On September 18th, multiple Five Eyes agencies issued a Joint Cybersecurity Advisory accusing the Chinese company Integrity Tech of compromising thousands of Internet-connected devices to create a botnet. The IP addresses used by the company were also reportedly utilized to access other operational infrastructure used in intrusion activities. The advisory cites Flax Typhoon, RedJuliett, and Ethereal Panda as the industry names for this threat group. At the same time, the FBI announced a disruption operation deployed against this botnet, noting that this threat group has successfully attacked several U.S. and foreign corporations, universities, government agencies, telecommunications providers, and media organizations.
Integrity Tech is also known in the industry as Yongxin Zhicheng (永信至诚科技集团股份有限公司). Founded in 2010, the company has nearly 500 employees, with 50 full-time developers and researchers, and has revenues of $56 million.
Many Chinese cybersecurity companies have been linked to hacking operations in the past or have provided support and talent to the Chinese government's cyber offensive units. However, the involvement of a company of this size is unprecedented, according to The Record. Consequently, this blog post aims at exposing the company's offensive genes and its links to Chinese intelligence agencies.
Note: This topic is not directly related to Transnational Repression. However, as discussed below, Integrity Tech has closed ties to the public security and state security apparatuses in the People's Republic of China (PRC), which are responsible for, among other things, the repression of dissidents at home and abroad.
The Company’s Offensive Genes
Integrity Tech specializes in simulation capabilities and is the leading cyber range company in the PRC. Its training services offer scenarios that it claims are very close to actual combat in the cyberspace.
To market its services, the company openly boasts of its front-line offensive hands-on experience. It claims on its website to have integrated offensive and defensive genes into the design of every security product, service and solution, so that the company as a whole has the ability to both attack and defend. In a recent public job posting, the company also attempts to attract future talent by stating, “If you want to be a wolf, or you are already a wolf, then join us, we will provide you with vast wilderness and fat lambs!”.
Integrity Tech’s founding is deeply tied to the history of offensive hacking in the PRC. In fact, it was founded by Cai Jingjing (蔡晶晶), who was part of the Green Army hacker community in the late 1990s and participated in the Patriotic Hackers campaign against the United States in the early 2000s as a member of the 0x557 hacker group. One of the company’s current directors, Fu Hao (付浩), is also a member of a Chinese hacking team called “Nu1L”. He has won several CTF (Capture the Flag) competitions and was a contributor to the book “Handbook for CTFers: Zero to One” written by “Nu1L”. He also wrote another book titled “Intranet Penetration System Construction”, which was prefaced by Cai Jingjing.
The fifth gathering of the hacking group 0x557. Cai Jingjing is possibly seated in the front row, sixth from the right. (Source)
Integrity Tech's workforce almost certainly includes other individuals with offensive background. For example, in online job postings, the company has sought candidates with experience in red team tool development, with practical penetration experience, a familiarity with social engineering attacks, with previous participation in various attack and defense competitions, with experience in reporting high-risk vulnerabilities and with expertise in smart hardware security or cracking. For one position, the company also gives preference to candidates that do not rely on specific tools to develop and use various techniques. This would include Living Off the Land (LOTL).
The KR Lab, which is a specific laboratory within the company, most likely plays a central role in its offensive operations. The FBI’s affidavit indicates that the KR Lab and an employee, identified only as INDIVIDUAL 1, are associated with the botnet operation. The KR Lab was founded shortly after the creation of Integrity Tech and focuses on AI research for network security attack and defense, as well as automated vulnerability mining and exploitation. According to the company’s website, it conducts research in the areas of APT attack analysis, 0-day vulnerability analysis and software reverse engineering. A job posting for a Binary vulnerability mining engineer with the Lab also points towards an interest in the Internet of Things (IoT).
The affidavit identifies a patent published on February 2nd, 2024, with Integrity Tech as the applicant, that is consistent with the implementation of a proxy service used in a botnet. The inventors are listed as managers of KR Lab and INDIVIDUAL 1. The patent, titled “A configuration method, device and computing device for a proxy node” (CN202311530002.7), was retrieved online. It lists the following individuals:
Cai Jingjing, the chairman for Integrity Tech;
Chen Jun (陈俊), the company’s vice president;
Zheng Hao (郑皓), identified online as a director for the KR Lab and a core technical staff for Integrity Tech;
Sun Yi (孙义), identified in 2018 as the director of the Chunqiu Teaching and Research Center, the learning platform for Integrity Tech. He has since become the director of the KR Lab. He has served as a judge in many hacking competitions, including for the Matrix Cup in 2024, along with the director of another Integrity Tech’s lab. The company also co-organized the Matrix Cup, which is the first Chinese hacking competition to include all three styles of challenges found in previous competitions;
Ren Jinkai (任金凯), identified online as a department manager in the company;
You Tengda (尤腾达);
Zhao Hualei (赵华磊);
Chen Jia (陈佳);
Given the way the affidavit is written, it is possible that INDIVIDUAL 1 is one of the last three people whose names are included in the patent.
Integrity Tech's Relationships with Cyber Units
Integrity Tech is linked to several Chinese intelligence and cyber agencies, through various partnerships and collaborations. According to cyber defense researcher Eugenio Benincasa, Integrity Tech was already known for these links before the Joint Cybersecurity Advisory was published, but the extent of these relationships has not yet been publicly presented.
The company has likely provided offensive capabilities to Chinese public security organizations. On its presentation page, Integrity Tech claims to have provided cybercrime intelligence collection and reconnaissance services for national, provincial and municipal institutions for many years, helping to solve a large number of cases. It says that through close cooperation with local public security institutions, it has made “contributions in assisting in combating cybercrime and maintaining the order of the cyberspace”. An archived version of Integrity Tech’s website states that KR Lab was behind these efforts. In 2016, the company boasted it had used its advanced penetration skills to hack into a gambling website with a server located overseas to obtain virtual identity information at the request of the Ministry of Public Security (MPS).
In the Chinese cyber ecosystem, hacking competitions are used to train participants and cultivate talent for recruitment by cybersecurity companies and government agencies. Integrity Tech claims to have supported more than 610 such security competitions. For example, in July 2021, it provided technical support for the 4th Red Hat Cup Cybersecurity Competition. Co-organized by the Guangdong Provincial Public Security Department, it was designed to implement “the "Red Hat" talent project strategy” of cultivating, selecting and providing cybersecurity professionals with practical skills for the Guangdong Province.
Integrity Tech also maintains relationships with the state security apparatus. Most notably, it is a Tier 2 technical support unit for the National Information Security Vulnerability Database (CNNVD), a body run by the Ministry of State Security (MSS) that collects vulnerabilities and pass them on to offensive units for future weaponization. For example, the KR Lab discovered a critical vulnerability in the D-Link DIR-645 router and reported it to the CNNVD, who published it in 2021. Of interest, Flax Typhoon used similar compromised routers for its botnet operations.
In addition to reporting vulnerabilities to the CNNVD, the company has a relationship with the China Information Security Evaluation Center (CNITSEC), the public facing name for the MSS’s 13th Bureau. In 2014, it established the Joint Laboratory for Cyberspace Security Technology Research with the Guangdong Information Security Evaluation Center, a provincial branch of the CNITSEC with close ties to the Guangzhou Boyu Information Technology Company, also known in the industry as APT3. Furthermore, in April 2024, Integrity Tech co-organized with the Guangdong Information Security Evaluation Center the semifinals of the “Great Wall Cup”, hosted by the CNITSEC.
Joint Laboratory for Cyberspace Security Technology Research between Integrity Tech and the Guangdong Information Security Evaluation Center (Source)
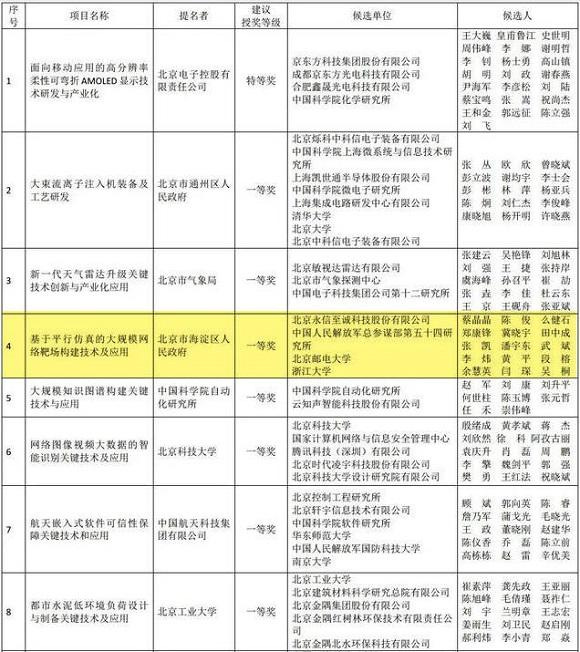
Finally, Integrity Tech is associated with military cyber forces. Its project called "Large-scale Network Range Construction Technology and Application Based on Parallel Simulation" was jointly developed with the Beijing University of Posts and Telecommunications, Zhejiang University and the 54th Institute of the People’s Liberation Army (PLA). This research center was previously under the Fourth Department of the PLA, and some of its members have been indicted in the U.S. in relation to the Equifax hack. Notably, the company tried to hide the real name of the PLA unit it was working with until it won an award for the project and the recipients were listed online in an news article.
Recipients for the Beijing Science and Technology Awards for 2019, including the project called "Large-scale Network Range Construction Technology and Application Based on Parallel Simulation" (Source)
This relationship with the PLA continues today. In 2024, the company was looking for a Military Sales Manager, responsible for bidding on military projects and coordinating project management with military units. In addition, in August 2024, Integrity Tech sponsored a youth competition to develop future cybersecurity talent. The participants received several consecutive days of hands-on professional training at three universities, including the Information Engineering University of the PLA’s Strategic Support Force (SSF).
Conclusion
While the attribution of an offensive operation to a Chinese cybersecurity firm of this size may be unprecedented, it should come as no surprise given Integrity Tech's offensive genes and ties to PRC intelligence and cyber agencies. The company publicly boasts of its offensive capabilities, and its KR Lab is actively involved in such research.
There are several other cybersecurity companies in the PRC that are as large or larger. Even with the public exposure of Flax Typhoon’s operations, they are unlikely to change their service offerings, given the environment they operate in and the incentives to actively contribute to the PRC’s national cybersecurity strategy. Other Chinese companies may therefore be exposed in the future for having offensive programs as part of broader services and products.